Let's Encrypt TLS certificate setup for Apache on Debian 7
Through Let's Encrypt, anybody can now easily obtain and install a free TSL (or SSL) certificate on their web site. The basic use case for a single host is very simple and straight forward to set up as seen here. For multiple virtual hosts, it is simply a case of rinse and repeat.
On older distributions, a bit more effort is required. E.g. on Debian 7 (Wheezy), the required version of the Augeas library (libaugeas0, augeas-lenses) is not available, so the edits to the Apache config files have to be managed by hand. Furthermore, for transitioning from an old HTTP based server, you need to configure the redirects for any old links which still might hard code "http" in the URL. Finally, there's some security decisions to consider when selecting which encryption protocols and ciphers to support.
Installation and setup
Because the installer has only been packaged for newer distributions so far, a manual download is required. The initial execution of the letsencrypt-auto binary will install further dependencies.
sudo apt-get install git
git clone https://github.com/letsencrypt/letsencrypt /usr/local/letsencrypt
cd /usr/local/letsencrypt
./letsencrypt-auto --help
To acquire the certificates independently of the running Apache web server, first shut it down, and use the stand-alone option for letsencrypt-auto. Replace the email and domain name options with the correct values.
apache2ctl stop
./letsencrypt-auto certonly --standalone --email johndoe@example.com -d example.com -d www.example.com
Unless specified on the command line as above, there will be a prompt to enter a contact email, and to agree to the terms of service. Afterwards, four new files will be created:
/etc/letsencrypt/live/example.com/cert.pem
/etc/letsencrypt/live/example.com/chain.pem
/etc/letsencrypt/live/example.com/fullchain.pem
/etc/letsencrypt/live/example.com/privkey.pem
If you don't have automated regular backup of /etc, now is a good time to at least backup /etc/letsencrypt and /etc/apache2.
In the Apache config for the virtual host, add a new section (or a new file) for the TSL/SSL port 443. The important new lines in the HTTPS section use the files created above. Please note, this example is for an older Apache version, typically available on Debian 7 Wheezy. See these notes for newer versions.
# This will change when Apache is upgraded to >2.4.8
# See https://letsencrypt.readthedocs.org/en/latest/using.html#where-are-my-certificates
SSLEngine on
SSLCertificateFile /etc/letsencrypt/live/example.com/cert.pem
SSLCertificateKeyFile /etc/letsencrypt/live/example.com/privkey.pem
SSLCertificateChainFile /etc/letsencrypt/live/example.com/chain.pem
To automatically redirect links which have hard coded http, add something like this to the old port *.80 section.
#Redirrect from http to https
RewriteEngine On
RewriteCond %{HTTPS} off
RewriteRule (.*) https://%{HTTP_HOST}%{REQUEST_URI} [R,L]
While editing the virtual site configuration, it can be useful to watch out for the logging format string. Typically the logging formatter "combined" is used. However, this does not indicate which protocol was used to serve the page. To show the port number used (which implies the protocol), change to "vhost_combined" instead. For example:
CustomLog ${APACHE_LOG_DIR}/example_com-access.log vhost_combined
To finish, optionally edit /etc/apache2/ports.conf, and add the following line to the SSL section. It enables multiple named virtual hosts over SSL, but will not work on old Windows XP systems. Tough luck.
<IfModule mod_ssl.c>
NameVirtualHost *:443
Listen 443
</IfModule>
Finally, restart Apache to activate all the changes.
apache2ctl restart
Verification and encryption ciphers
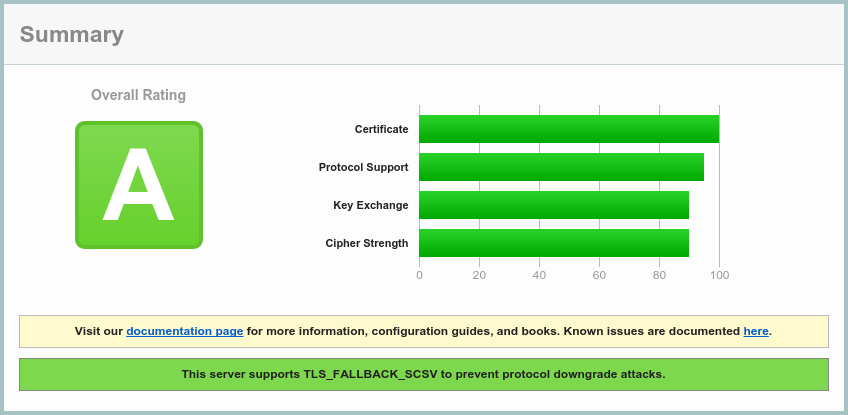
SSL Labs has an excellent and comprehensive online tool to verify your certificate setup. Fill in the domain name field there, or replace your site name in the following URL, and wait a couple of minutes for the report to generate. It will give you a detailed overview of your setup, what works, and what is recommended to change.
https://www.ssllabs.com/ssltest/analyze.html?d=example.com
Ideally, you'll get a grade A as shown in the image below. However, a few more adjustments might be required to get there. It typically has to do with the protocols and ciphers the web server is configured to accept and use. This is of course a moving target as security and cryptography research and attacks evolve. Right now, there are two main considerations to make: All the old SSL protocol versions are broken and obsolete, so should be disabled. Secondly, there's an attack on the RC4 cipher, but disabling that is a compromise, albeit old, between its insecurity and the "BEAST" attack. Thus, disabling RC4 now seems to be preferred.
Taking all this into account, the recommended configuration for Apache and OpenSSL as it stands excludes all SSL versions, as well as RC4 versions. This should result in a forward secrecy configuration. Again, this is a moving target, so this will have to be updated in the future.
To make these changes, edit the Apache SSL mod file /etc/apache2/mods-available/ssl.conf directly, or update the relevant virtual host site config file with the following lines.
SSLHonorCipherOrder on
SSLCipherSuite "EECDH+ECDSA+AESGCM EECDH+aRSA+AESGCM EECDH+ECDSA+SHA384 EECDH+ECDSA+SHA256 EECDH+aRSA+SHA384 EECDH+aRSA+SHA256 EECDH+aRSA+RC4 EECDH EDH+aRSA RC4 !aNULL !eNULL !LOW !3DES !MD5 !EXP !PSK !SRP !DSS !RC4 !ECDHE-RSA-RC4-SHA"
SSLProtocol all -SSLv2 -SSLv3
Restart Apache, and regenerate the SSL Labs report. Hopefully, it will give you a grade A.
Final considerations
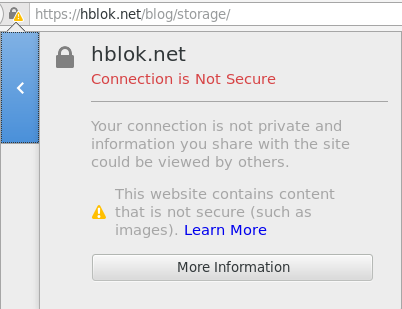
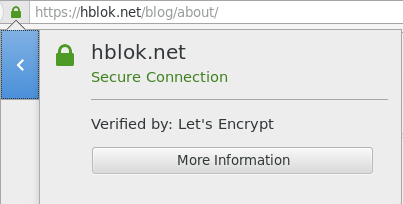
Even with all the configuration above in place, the all-green TSL/SSL security lock icon in the browser URL bar, as seen below right, might be elusive. Instead a yellow warning like the on in the image to left might show. This could stem from legacy URLs which have hard coded the http protocol, both to the internal site and external resources like images, scripts. It's a matter of either using relative links, excluding the protocol and host altogether, absolute site links, inferring the protocol by not specifying it, or hard coding it. Examples:
<img src="blog_pics/ssl_secure.png">
<img src="/blog_pics/ssl_secure.png">
<img src="//i.creativecommons.org/l/by-sa/3.0/88x31.png">
<img src="https://i.creativecommons.org/l/by-sa/3.0/88x31.png">
On a blog like this, it certainly makes sense to put in some effort to update static pages, and make sure that new articles are formatted correctly. However, going through all the hundreds of old articles might not be worth it. When they roll off the main page, the green icon will also show here.